What viruses affect 3Ds Max?
Nowadays it's hard to find a CG industry specialist who doesn't use thematic forums, 3D-stocks and a huge number of other online resources. And every time you risk corrupting your project with spyware, what may entail a lot of unpleasant issues, sometimes with a complete loss of the ability to continue working.
Just open an infected *.max once, or add such a 3d model to your own scene.
Here we'll look in detail at what badly code exists and how dangerous they are.
ALC BETACLEANER
ALC is most likely to have spread through free 3D models. It is essentially a script (Maxscript) that corrupts program settings. Once your soft is damaged, all your *.max scenes risk infection when opening.

Script creates hidden files inside startup folder of your 3ds Max, with titles vrdematcleanbeta and the extensions ms, mse, msex
Warning!
You will not see hidden files unless displaying hidden data sets is turned on. This needs to be enabled in your system preferences.
By infecting ALC, you may encounter such troubles: scenes will not open and fly out, empty helpers with "¡¡×ý×û" and "×þ×û" names will be generated, you will be unable of saving, Ctrl+Z does not function, Maxscript will show errors, lighting sources and cameras may be removed spontaneously. Materials change their properties. Closing 3D Max will select "Don't Save", but it will still be saved. The remaining scripts of this software will have executable code written into them, and any scene data may be corrupted.
CRP BSCRIPT & ADSL BSCRIPT
CRP is similarly a dangerous code (Maxscript) that damages your program and its other scripts.
What to expect after being infected with this spyware:
- Ctrl+Z doesn't work when you switch between Viewports;
- Light sources are not displayed, and sometimes deleted completely;
- Shaders are deleted;
- Some geometry was removed on its own.
ALC2 ALPHA
In addition to everything described earlier, it is capable of creating various parameters in 3Ds Max.
These script files also have stealth functions and are found in the launch directory of your 3dsMax, with the titles vrdematcleanalpha, vrdestermatconvertor and vrayimportinfo having the extensions ms, mse, msex.
Doing so creates a lot of ALC BETACLEANER-like problems.
ALC3 ALPHA
Another variation of ALC BETACLEANER, more advanced.
Malware updates and changes!
Problems related to ALC infection:
- 3Ds Max fails, and some scenes are not available;
- Helper objects generated;
- Unable a Ctrl + Z;
- Maxscript indicates bugs;
- The settings of the renderer (V-Ray) change on their own. Spontaneous changes in v-ray frame buffer parameters, global illumination settings, etc;
- Shader configurations change spontaneously.
The script also collects information and emails it from the email address sss777_2000@126.com to the email address rrr888_3000@126.com. The leakage of such data and properties is revealed:
- Images taken via your VFB;
- Your location details: ip, mac address
- Specifications about your computer such as data hard drive, installed memory, processor power.
- Information about software, for example the 3Ds Max edition;
- ALC3 updated by downloading renewal from the maxscript.cc site
- Generates files on your PC: vrdematpropalpha with the extensions ms, mse, msex inside the startup folder of your 3dsMax software.
DESIRE FX CA
If you become infected, you risk encountering this:
- Object titles are prefixed by a prefix;
- The operand that contain the announcement words appear;
- Ads are also recorded in the File Info document;
- Braking in the viewport.
AD WEB CA
Difficulties that arise due to this malware:
- Maxscript website ads as a Web page;
- Adware text objects show up;
- Braking in the viewport.
You can enable the blocking of advertising sites directly in system settings. In order do this, you must perform some elementary actions:
- Search for a document called hosts, located here: C:/WINDOWS/system32/drivers/etc/hosts Use Notepad to open it;
- Place the text down a document:
127.0.0.1 www.3dsmj.com
127.0.0.1 3d.znzmo.com
- Don't forget to restart your computer when you save the document.
PHYSXPLUGINMFX
PhysXPluginMfx (another version of ALC2, ALC, CRP and ADLS) initially created via hackers as an industrial espionage tool to target big businesses. It is distributed by phishing sites via external plugins. It corrupts 3Ds Max configuration as well as damages other data in the software environment. Collects data about user machines. In fact, this information is transmitted through the C&C servers positioned within the Republic of Korea.
It generated files that execute malicious code. It is in the 3ds Max autoloader and is called PhysXPluginStl with the extensions ms, mse.
What it can do:
- Encoding "*.mse" (base64 encoding, .NET 4.5 assembler);
- Infection of your "*.max";
- Transmission of your personal information.
ALIENBRAINS (MSCPROP.DLL)
ALIENBRAINS is most often damaged through standard models that have been online downloaded via unverified sites. This malware corrupts the installation files of the program and, therefore, the scene on your computer.
Alienbrains may delay the scene. It takes an unacceptably slow time for opening and saving data sets.
"Runtime error: FileStream cannot create..." - such error messages appear during opening of a damaged file.
From the program root a filename mscprop.dll is created. This happens when Account Control is turned off in settings.

Make sure you understand that your Alienbrains program is corrupt If you experience any of the following symptoms:
- You found mscprop.dll in the root directory of 3Ds Max;
- Opening and save for a very long duration;
- Objects spontaneously get unnecessary attributes;
- In rootcene and callback you detected undesirable properties;
- Bug in Maxscript (view screenshot);
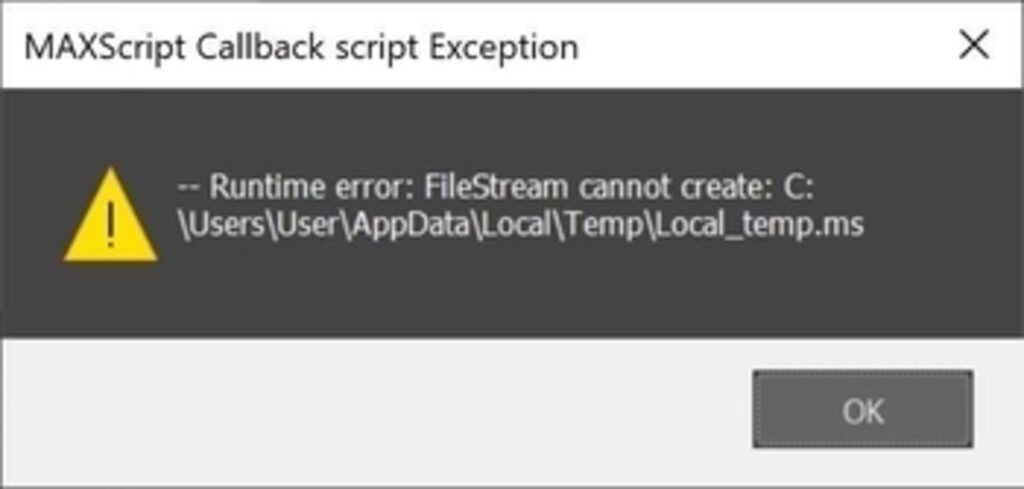
- Failed Ctrl+Z.
This malicious program is located inside the Temp folder named Local_temp with ms, mse extensions, as well at the root of the program - mscprop.dll, also in the stdplugs folder - PropertyParametersLocal.mse file.
KRYPTIK CA
Just like the previous one, this malicious code installation data from your software and files. Infection also usually occurs when 3D models taken from unverified resources get infected.

KRYPTIK CA affects opening speed of scenes.
What it does:
- Scenes take a very long time to open and save, including long autosave times.
- Different attributes may be spontaneously generated for objects;
- Undesirable features of TrackViewNodes.AnimLayerControlManager and callback can be generated;
- Malicious code is running (base64 encoding of .NET 4.5 assembler from *.dll file that contains).
To date, no precise threat of this *.dll has been identified, but work is underway to decrypt the code.
HOW DO I KNOW IF A VIRUS IS PRESENT?
It is possible to detect each of these malicious scripts on your PC by yourself via simple steps. Open MaxScript Listener, then copy the line corresponding to the spyware you wish to test for by pasting it in (below you can see the lines for each malware detection in this way) then press Enter. By evaluating this command, you check for a virus. False answer means it is not corrupted or viral, given that the answer would be True!
Checking ALC betaclenaer
(globalVars.isGlobal #AutodeskLicSerStuckCleanBeta)
Checking ADSL bscript
(globalVars.isGlobal #ADSL_BScript)
Checking CRP bscript
(globalVars.isGlobal #CRP_BScript)
Checking ALC2 alpha
(globalVars.isGlobal #AutodeskLicSerStuckCleanAlpha)
Checking PhysXPluginMfx
(globalVars.isGlobal #physXCrtRbkInfoCleanBeta)
Checking ALC3 alpha
(globalVars.isGlobal #AutodeskLicSerStuckAlpha)
Checking Alienbrains
(try(TrackViewNodes.TVProperty.PropParameterLocal.count >= 0) catch(false))
Checking Kryptik CA
((try(TrackViewNodes.AnimLayerControlManager.AnimTracks.ParamName) catch(undefined)) != undefined)
To detect some malware there is no need to perform a special scan, its presence can be seen directly in the program.
Presence AD Web CA
Maxscript will advertise sites: 3dsmj and 3d.znzmo.


Presence Desire FX CA
Every object is prefixed with "desirefx".

Important information!
Unfortunately, not all malware is detectable and removable by yourself. But Prune Scene easily fixes this trouble.
HOW TO CLEAR MYSELF OF MALWARE?
To keep yourself safe from infection or to clear a scene that is already sick, try Prune Scene.
Please enable the function Active Protect, all existing malicious scripts automatically removed during opening of infected files.

Prune Scene does not need to be run manually unlike other sub scripts. It is always a sure result, since chances are that you won't forget to check some 3D models. This is relevant especially for large firms, in which several specialists may work on the same scene. In addition, Prune Scene removes all known virus modifications, and there is no need to use several scripts to detect different types of malicious scripts.
Download Prune Scene
Note!
Prune Scene is free!
All 3D models uploaded on 3DBaza are obligatory checked for the presence of malicious viruses, damaged models are not allowed for publication. Downloading models from our site you can be sure that they will not harm your software and your projects.
Information for this article was provided courtesy of MastaMan

